Crime Prevention Through Environmental Design (CPTED) is a method to reduce crime by improving visibility, controlling access, and maintaining spaces effectively. By applying CPTED principles, you can make your property safer and less attractive to criminals. Here’s what you need to know:
- Core Principles: Focus on natural surveillance, access control, territorial boundaries, active use of spaces, and regular upkeep.
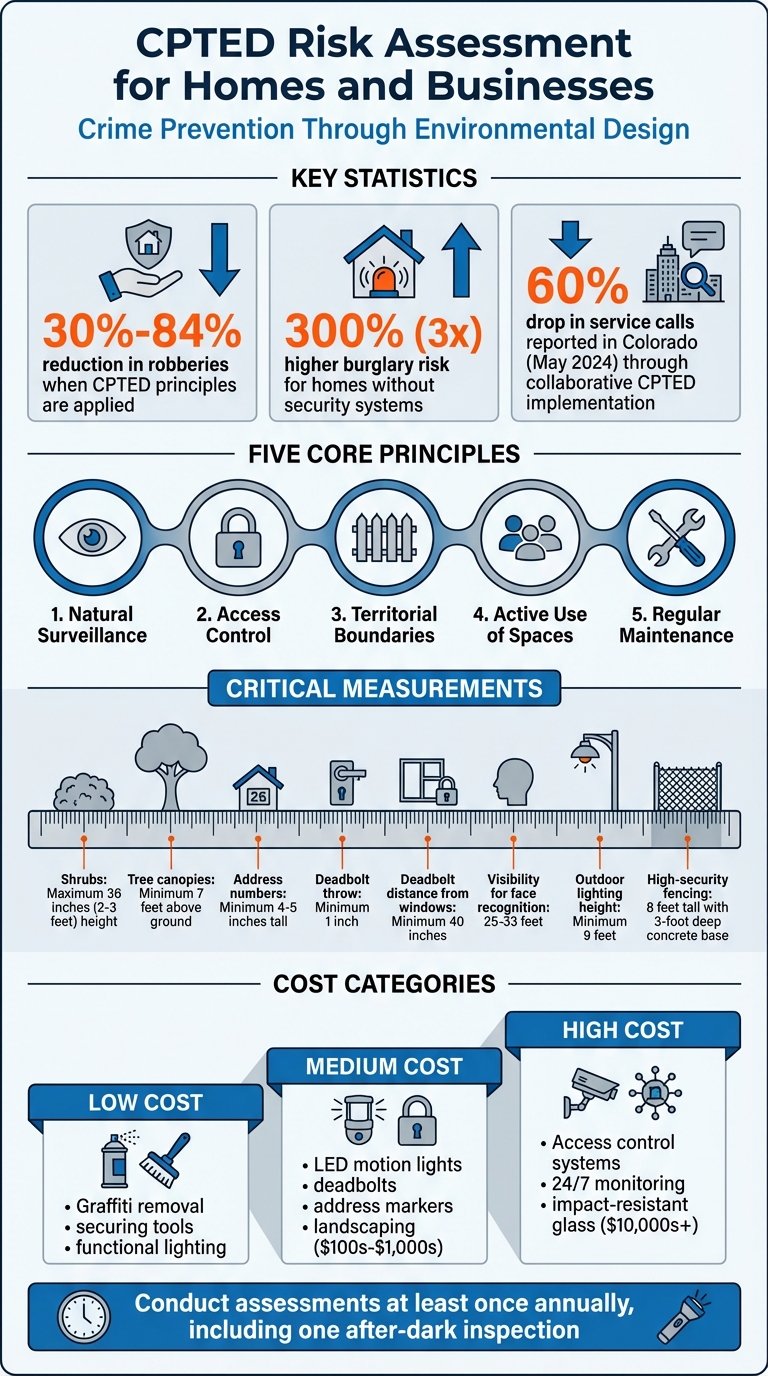
- Benefits: Properties using CPTED report 30%-84% fewer robberies. Homes without security systems are three times more likely to be targeted.
- Application: For homes, prioritize visibility from the street and secure entry points. For businesses, ensure clear sightlines, controlled entrances, and defined boundaries.
- Preparation: Conduct walkthroughs, gather data like crime reports, and use tools like checklists and cameras to identify weak spots.
- Improvements: Address vulnerabilities with low-cost fixes (e.g., better lighting), medium-cost upgrades (e.g., deadbolts), or high-cost investments (e.g., advanced security systems).
Start by assessing your property, documenting risks, and prioritizing solutions. Whether for a home or business, CPTED helps create safer, more secure spaces.
CPTED Risk Assessment: Key Statistics and Implementation Guidelines
CPTED explained for Security Professionals | Crime Prevention Guidelines, Standards & Certification
Preparing for a CPTED Risk Assessment
Proper preparation is key to successfully applying CPTED (Crime Prevention Through Environmental Design) strategies to improve security. Plan your walkthrough carefully to spot vulnerabilities and address them effectively.
Defining Objectives and Scope
Start by setting clear objectives for the space. This helps you think about how the area is actually used, not just its intended purpose. For example, a wall designed for security might unintentionally become a spot for loitering if you don’t account for its practical use.
Your goals will depend on the type of property. Homeowners might focus on reducing burglary risks and improving visibility in their neighborhood, while business owners may prioritize meeting legal requirements. Keep in mind that local regulations could mandate periodic assessments to maintain compliance.
Next, determine the scope of your assessment. Will you limit it to the building’s perimeter, or include areas like parking lots, alleys, loading docks, and waste disposal zones? High-risk areas, such as parking lots and alleys, deserve particular attention. Make sure to do at least one inspection after dark to check how well the lighting works .
Once your objectives and scope are outlined, you can move on to gathering the information needed for a comprehensive evaluation.
Gathering Required Information
Before heading to the site, collect important data. Reach out to local law enforcement for crime reports to identify patterns, such as common break-in times or frequently targeted entry points.
Pay attention to details like landscaping, address visibility, and door lock specifications:
- Shrubs should be trimmed to a maximum height of 36 inches.
- Tree canopies should start at least 7 feet above the ground.
- Address numbers should be at least 4 inches tall and clearly visible from the street.
- Exterior doors should have deadbolts with a minimum one-inch throw, installed at least 40 inches away from nearby windows.
Also, interview occupants to uncover potential security issues that might otherwise go unnoticed. This information will be crucial when conducting your onsite evaluation.
Tools and Resources for the Assessment
Gather the tools you’ll need: a flashlight, measuring tape, camera, and a standardized CPTED checklist. The checklist should cover key principles like natural surveillance, access control, territorial reinforcement, activity support, and maintenance .
Review existing security policies and incident reports before beginning your walkthrough. This will give you a clearer picture of current practices . If the property has security cameras, confirm they provide adequate coverage and ensure staff are trained to use them effectively. Take note of lighting types – LEDs are generally a better choice than Low Pressure Sodium bulbs because they offer superior color rendering.
In May 2024, the Colorado Office of Research & Statistics highlighted the success of CPTED strategies when law enforcement and business owners worked together. They reported a 60% drop in service calls, achieved by combining physical design changes with "social management" or activity support. Statistical Analyst Mindy Duong emphasized the importance of this collaborative approach.
With clear objectives, detailed data, and the right tools, you’ll be well-prepared to implement CPTED principles and improve your property’s security.
Applying CPTED Principles to Residential Properties
Improving Natural Surveillance
Make sure all entry points to your home are visible from the street, allowing faces to be recognized from a distance of 25–33 feet.
Keep landscaping in check by trimming shrubs to stay under 2 feet, raising tree branches to at least 6 feet, and avoiding hedges or trees within 6 feet of doorways. Remove any large rocks near windows to prevent their use as tools by intruders.
"Natural Surveillance is a design concept that promotes the ability to see and be seen. If Natural Surveillance is limited, pedestrians and other users of the space may feel unsafe and anxious… while potential offenders may feel more comfortable." – Seattle Police Department
Ensure windows remain unobstructed by large plants, signs, or heavy curtains to maintain a clear view of the street and parking areas. If you have a front yard fence, keep it no taller than 36 inches and avoid solid designs to eliminate hidden spots between your home and the street.
Install outdoor lighting at a height of at least 9 feet to cover more area and reduce the risk of tampering. Use motion sensors for less-frequented areas like side yards and dusk-to-dawn sensors near entrances for consistent illumination. Opt for LED lights with good color rendering to help identify clothing and physical details at night. Position lights downward to minimize glare.
Once visibility is optimized, focus on securing access points to further reduce the likelihood of intrusions.
Strengthening Natural Access Control
Combine access control measures with the surveillance strategies outlined above. Identify all potential entry points – doors, windows, driveways, and side gates. Ensure your driveway is visible from at least one window inside your home.
Plant low, thorny bushes like roses or raspberries under ground-floor windows, keeping them between 2–3 feet high. This deters intruders without blocking visibility.
For fences, choose open designs such as wrought iron instead of solid panels to maintain visibility while controlling access. If greater security is required, fences should be at least 8 feet tall and installed with bases set in 3-foot deep trenches filled with concrete to prevent digging.
Inspect gates and fences regularly – monthly self-checks and annual professional inspections are recommended. Locksmith services like Sherlock’s Locksmith can ensure your locks meet current safety standards and suggest upgrades if necessary.
Make sure your house numbers are at least 5 inches high and made from non-reflective material so they remain easy to read.
Territorial Reinforcement and Maintenance
Establishing clear boundaries around your property helps signal active management. Use low fences (under 36 inches), flower beds, or different pavement styles to mark where public sidewalks end and your private space begins.
"Property that has been properly defended suggests to a criminal that a legitimate citizen may be near to witness the crime and call the police. Property that is not defended tells the criminal that no one is watching." – Town of Danville CPTED Handbook
Stay on top of maintenance to send a clear message. Pick up litter promptly, fix broken fences or windows without delay, and remove graffiti as soon as it appears. A well-maintained lawn and flower beds signal active occupancy and regular monitoring.
Don’t leave ladders, tools, or valuable equipment unsecured outside, as these items could aid intruders. Keep your mailbox close to the house and clearly marked with your address. Even simple activities like gardening or sitting on your porch create a natural presence that deters unwanted behavior.
Posting signs like "Private Property" or "No Trespassing" can also reinforce that the area is actively managed and off-limits to unauthorized individuals.
sbb-itb-643e28e
Applying CPTED Principles to Commercial Properties
Improving Natural Surveillance in Businesses
To enhance natural surveillance, position workstations and reception areas near windows that provide a clear view of parking lots and nearby streets. According to CPTED guidelines, window signage should cover no more than 10% of the window space, ensuring unobstructed sightlines.
"CPTED works by decreasing a criminal’s ability to commit crime and increasing the chances that legitimate citizens will see the crime." – Danville CPTED Handbook
Inside the building, keep shelving and displays at or below 5 feet in height to maintain visibility across the space. Elevate front counters for the same reason. In parking garages, use light-colored paint on walls and ceilings to brighten the area and install convex mirrors at corners to reduce blind spots.
For outdoor areas, trim shrubs to a maximum height of 36 inches and ensure tree canopies start at least 7 feet above the ground. Remove potential hiding spots, such as garbage bins, electrical boxes, or dense vegetation near entrances and walkways. Use LED lighting to illuminate spaces effectively, with coverage extending up to 25 feet.
These visibility strategies create a solid foundation for implementing stronger access control and boundary measures.
Implementing Access Control and Target Hardening
Once clear sightlines are established, focus on controlling access points. Limit public entry to essential doors and monitor these areas consistently. Exterior doors should be solid-core or metal-clad and equipped with single-cylinder deadbolts (with at least a one-inch throw) placed at least 40 inches away from windows.
Keyless entry systems are an effective way to prevent unauthorized key duplication. Be sure to update access codes immediately following any staffing changes.
Use clear, bold signage to direct visitors to proper entrances and clearly mark "employee-only" areas. This makes unauthorized access more noticeable. Avoid propping open doors, even for short periods, as this creates an easy entry point for intruders. Equip all windows, including those in separate storage facilities, with secondary locking mechanisms for added security.
Reinforcing Territorial Boundaries and Maintenance
Establishing clear property boundaries is essential. Use bollards, decorative fencing, low walls, or distinct paving patterns to signal where public spaces end and private property begins. These physical markers guide visitors to the correct entrances and discourage loitering in restricted areas. Clearly label visitor and employee parking zones for further clarity.
"If a property looks loved and cared for, someone is bound to notice when trouble is afoot." – Lori Kaye Lodes, Deep Sentinel
Maintenance plays a key role in security. Address issues like burnt-out lights, broken locks, or graffiti promptly, as neglect can attract criminal activity. Follow the "two-foot, six-foot rule" for landscaping – keep shrubs trimmed to 2 feet and ensure tree canopies start at 6 feet or higher. This preserves visibility while defining property lines. Lastly, use signage to identify your business, outline acceptable activities, and provide instructions for reporting suspicious behavior.
Documenting Risks and Prioritizing Security Improvements
Creating a Risk Register
Once you’ve identified vulnerabilities during your CPTED walkthrough, it’s time to organize your findings systematically. A risk register helps you turn those observations into a clear and actionable plan. Start with a simple spreadsheet, noting each asset, its vulnerability, the related CPTED principle, and your proposed solution. Add ratings for likelihood and impact to help prioritize.
While conducting your walkthrough, use a straightforward "Yes/No/NA" survey format. Any "No" response should be added to your risk register. For example, you might uncover gaps in natural surveillance or issues with access control. The Security Executive Council advises:
"Highest priority should be given to those areas that have high values for probability, criticality, and vulnerability".
Focus your attention and resources on these high-priority areas, as they represent the most urgent security concerns.
To ensure a balanced approach, link each identified vulnerability to one of the Four Pillars of Building Security:
- Deterrence: Discouraging threats.
- Detection: Identifying activity.
- Delay: Slowing intruders.
- Response: Managing incidents.
This framework ensures that your security measures address all critical aspects.
Categorizing Improvements
Once vulnerabilities are identified, group potential improvements based on cost: low, medium, and high.
- Low-cost changes: These are often quick fixes or simple maintenance tasks. Examples include removing graffiti promptly, locking up ladders and tools, or ensuring lights are functional.
- Medium-cost upgrades: These typically fall in the range of a few hundred to a few thousand dollars. Examples include installing LED motion-activated lights, adding visible address markers, trimming shrubs to a height of 36 inches for better visibility, or upgrading standard locks to deadbolts.
- High-cost investments: These might include advanced systems like integrated access control, 24/7 professional monitoring, or impact-resistant glass. These measures often require tens of thousands of dollars and should be reserved for vulnerabilities with high ratings for likelihood, impact, and vulnerability. For context, homes without security systems are 300% more likely to be burglarized, and applying CPTED principles has been shown to reduce robberies by 30% to 84%.
After identifying cost-effective measures, consult experts to ensure proper implementation.
Partnering with Security Professionals
To enhance your CPTED efforts, consider working with security professionals. Locksmiths, for instance, can verify the proper installation of physical security features. For example, they ensure deadbolts are installed correctly, with strike plates secured to the door frame. Locksmiths can also rekey locks after a move or staff changes, protecting against unauthorized access by previous key holders.
For commercial properties, security specialists can recommend hardware that meets regulatory standards like HIPAA or OSHA and provide ongoing maintenance that in-house teams may not be equipped to handle. In Pittsburgh, PA, Sherlock’s Locksmith offers services such as security assessments, lock upgrades, access control installations, and emergency support. Their certified technicians can review your risk register and suggest CPTED-aligned solutions tailored to your budget.
Make it a habit to conduct a physical security risk assessment at least once a year. This allows you to address new threats and adjust priorities as your property, neighborhood, or business needs evolve. Security is not a one-time effort – it’s an ongoing process that adapts to changing circumstances.
Conclusion
A CPTED risk assessment transforms security from being just reactive to a proactive approach, using smart design principles to discourage crime. By focusing on natural surveillance, territorial reinforcement, access control, and maintenance, you create multiple layers of deterrence that make your home or business far less appealing to criminals.
The numbers speak for themselves: CPTED strategies have been shown to reduce robberies by 30%–84%, while homes without security systems are three times more likely to be burglarized. This highlights the importance of having a dynamic, adaptable security plan.
Make it a habit to update your risk register regularly – at least once a year or whenever significant changes occur. As Ed Newman from Overton Security puts it:
"A security plan that isn’t regularly updated, tested, and re-evaluated is practically guaranteed to fail when you need it most".
Enlisting professional help can take your efforts even further. For example, in Pittsburgh, PA, Sherlock’s Locksmith offers certified technicians who can assess your risk register, suggest CPTED-compliant hardware upgrades (like deadbolts with a one-inch throw), and ensure your security measures stay up to date.
Don’t wait – start your assessment today. Walk through your property, identify vulnerabilities, and prioritize fixes based on their potential impact. Whether you opt for affordable DIY improvements or work with security experts for a more comprehensive plan, every action you take strengthens the safety and peace of mind for you and your property.
FAQs
How can I assess and improve my home’s security using CPTED principles?
To improve your home’s security using Crime Prevention Through Environmental Design (CPTED) principles, start by taking a close look at your property. Walk around and spot areas that might make your home vulnerable. For instance, overgrown shrubs or poorly lit spaces can create hiding spots. Address these issues by trimming vegetation and installing motion-sensor lighting to boost visibility and natural surveillance.
Next, inspect your access points, such as doors, windows, and gates. Make sure they’re secure and easy to monitor. If there are hidden entry routes, consider adding locks or placing clear signage to discourage intruders. You can also reinforce the property’s boundaries with visible markers like house numbers or strategic landscaping to project a sense of ownership, which can deter unauthorized access.
Lastly, focus on straightforward, budget-friendly upgrades. Install deadbolts, replace solid fences with open designs to improve sightlines, or prune bushes regularly. Once you’ve made these adjustments, revisit your property from time to time to ensure your measures are still effective and align with CPTED guidelines.
What are some affordable ways to improve my home’s or business’s security using CPTED principles?
There are plenty of affordable ways to boost security by applying Crime Prevention Through Environmental Design (CPTED) principles. Start by keeping shrubs and trees neatly trimmed to ensure clear sightlines and better visibility around your property. Consider swapping out solid fences for open or low-profile designs to allow for natural surveillance. Adding motion-activated lighting is another cost-friendly option that can discourage intruders while lighting up key areas during the night.
Make sure vehicles and walkways are placed in well-lit, open areas to minimize potential hiding spots. Simplifying your landscaping or reshaping it to remove areas where someone could hide can also go a long way in enhancing safety. These straightforward adjustments can help create a more secure space for your home or business.
How often should I review and update my CPTED security plan?
It’s important to regularly revisit your CPTED (Crime Prevention Through Environmental Design) security plan to ensure it stays effective and adapts to any changes in your property or its surroundings. While there’s no one-size-fits-all timeline, many security professionals recommend reviewing your plan every year or whenever significant changes occur. These changes might include renovations, new tenants moving in, or noticeable shifts in neighborhood safety trends.
Staying on top of your security plan allows you to identify and address vulnerabilities early, helping to create and maintain a safer environment for your home or business.









