Behavioral analytics is changing how organizations approach security. Instead of relying on outdated methods that miss subtle threats, it focuses on identifying unusual behavior. Here’s why this approach matters:
- Real-Time Threat Detection: Flags unusual activity, like odd login times or large data downloads, using AI and machine learning.
- Fewer False Alarms: Reduces unnecessary alerts by analyzing context, cutting false positives by nearly 38%.
- Better Insider Threat Detection: Identifies risks from within by spotting deviations in user behavior, such as unexpected file access.
- Simplified Compliance: Automates monitoring and reporting to meet regulations like GDPR and HIPAA.
- Faster Incident Response: Prioritizes critical threats so teams can act quickly, reducing response times.
Behavioral analytics combines data and AI to strengthen security, helping organizations detect threats faster and more accurately while reducing noise for security teams.
1. Real-Time Threat Detection
Real-time monitoring and anomaly detection
Behavioral analytics works by collecting data from endpoints, network traffic, and logs to create a baseline of what "normal" behavior looks like for each user and system entity. Using machine learning algorithms like k-means, DBSCAN, or autoencoders, it compares real-time activity against these baselines to identify unusual patterns. For instance, if an employee suddenly downloads a large amount of sensitive data, logs in from an unfamiliar location, or accesses systems at odd hours, the system flags this activity for further investigation.
This method can uncover threats that traditional signature-based tools often overlook. As Sharon Abraham Ratna from ManageEngine points out:
Behavioral analytics isn’t just another layer in your security stack. It’s your best shot at catching what your other tools miss.
This immediate detection is crucial for prioritizing and responding to potential threats.
Risk scoring engines play a key role by ranking anomalies based on factors like asset importance and user privilege levels. Alerts tied to critical systems or high-privilege accounts are given more weight, helping SOC analysts focus on the most pressing risks.
2. Fewer False Alarms
Cutting Down on False Positives
One of the biggest headaches for security teams is dealing with alerts that turn out to be harmless. Traditional security tools often rely on rigid "if-then" rules – like flagging any login attempt after five failed tries. The problem? These systems can confuse genuine user mistakes with actual threats, creating a flood of unnecessary alerts.
Behavioral analytics takes a smarter route by considering the context behind each action. Instead of flagging every anomaly, it evaluates behavior based on factors like role, location, and typical activity patterns. For instance, a developer working on code repositories at midnight might be completely normal, but the same behavior from someone in the finance department could raise a red flag. By comparing users to their peers in similar roles, this approach avoids the pitfalls of one-size-fits-all rules and significantly reduces false alarms.
Research shows that behavioral analytics can cut false positives by nearly 38% while maintaining an impressive 94.7% accuracy rate for identifying genuine threats. As Fidelis Security explains:
Instead of flagging every small deviation, behavioral analytics weighs the risk over time. It builds up evidence and assigns dynamic risk scores that reflect how severe, frequent, or suspicious an anomaly really is.
This kind of precision not only reduces noise but also strengthens real-time threat detection, improving overall security responsiveness.
Better Use of Resources
Fewer false alarms mean security teams can finally focus on what truly matters. When analysts are bogged down chasing harmless alerts, they risk overlooking real threats and can quickly burn out from "alert fatigue." Behavioral analytics automatically filters out irrelevant alerts, freeing up your team to concentrate on high-priority incidents.
To keep the system sharp, continuous feedback from analysts is crucial. This feedback helps refine the model over time, ensuring it learns from past mistakes and avoids repeating them. Additionally, scheduling quarterly baseline reviews ensures the system stays in sync with changing business operations, avoiding unnecessary alarms caused by "behavioral drift".
3. Better Detection of Insider Threats
Detection Methods
Insider threats are notoriously difficult to tackle. Unlike external attackers, insiders operate with legitimate credentials and authorized access, making it easier for them to navigate systems without setting off traditional alarms. It’s no surprise that about 30% of CISOs now rank insider risks as one of their top security concerns. On top of that, the financial toll is significant – the average cost of an insider threat incident hit $15.38 million in 2022.
One of the most effective tools for addressing this challenge is behavioral analytics. By analyzing patterns like login times, file access habits, and network usage, these systems create a baseline for normal user behavior. When someone deviates from their usual patterns – say, a marketing employee suddenly runs intensive queries or downloads an unusually large number of files – the system flags the activity immediately. Sharon Abraham Ratna from ManageEngine explains it best:
"Behavioral analytics helps you catch what traditional tools miss by analyzing subtle shifts in user and network behavior."
This approach makes it possible to identify threats that might otherwise slip under the radar.
Real-Time Monitoring and Anomaly Detection
Building on behavioral analytics, real-time monitoring takes things a step further by actively scanning for suspicious activity. Examples include off-hours logins, access from unexpected locations, mass file deletions, or attempts to enter sensitive directories. Each anomaly is assigned a risk score, factoring in the sensitivity of the affected assets and the user’s level of access.
The system also tracks lateral movement – when an individual or compromised account starts accessing systems outside their usual scope. To fine-tune detection, peer-based comparisons come into play, helping differentiate between legitimate changes in responsibility and genuinely suspicious behavior.
The results speak for themselves: one organization that adopted behavioral analytics reported a 70% reduction in the time it took to detect insider anomalies. This kind of precision not only enhances security but also minimizes the potential damage from insider threats.
4. Easier Compliance and Audit Support
Regulatory Compliance Support
Meeting regulatory standards like GDPR, HIPAA, and SOC 2 requires clear, auditable proof of continuous monitoring. Behavioral analytics tools make this easier by generating detailed logs, sending real-time alerts, and even offering data masking features. These tools can identify unauthorized access to sensitive data or misuse of privileged accounts, ensuring compliance with privacy and security rules. Some advanced systems go a step further by masking sensitive information based on user roles, adding another layer of protection to meet strict privacy regulations. This automation simplifies compliance efforts and ensures organizations are always prepared for audits.
Optimized Resource Allocation
Automated reporting also plays a crucial role in saving time during audits. By centralizing investigation materials and forensic evidence in case management systems, these tools eliminate the need for manual log reviews and periodic spot-checks. Continuous monitoring creates detailed audit trails that document what data was accessed, when, how, and why, making it much easier to manage and present during an audit. This reduces the manual workload and ensures the entire process runs more efficiently.
sbb-itb-643e28e
User and Entity Behavior Analytics (UEBA): AI-Powered Cybersecurity & Threat Detection
5. Faster Incident Response and Better Resource Use
Behavioral analytics works by constantly comparing current activity against established baselines, flagging any deviations as they happen. For instance, if someone logs in at an unusual time or transfers an unusually large amount of data, the system sends out immediate alerts. This real-time detection allows security teams to address threats in minutes rather than hours or even days, significantly reducing dwell time. This quick action not only limits the time threats linger but also helps teams manage their resources more effectively.
By automating repetitive tasks and assigning risk scores, behavioral analytics ensures that security teams focus their efforts where it matters most. These risk scores take into account factors like the sensitivity of the asset and the user’s level of access, helping analysts zero in on the most critical threats.
As ManageEngine puts it:
Behavioral analytics adds a layer of context to these alerts, enabling your SOC team to prioritize high-risk threats while filtering out noise. This not only improves response times but also optimizes resource allocation, ensuring the team focuses on genuine risks.
With fewer distractions from low-priority alerts, analysts can spend more time on proactive threat hunting and strengthening the organization’s overall security. This leads to better efficiency in handling incidents and a stronger defense against potential threats.
Combining Behavioral Analytics with Physical Security Systems
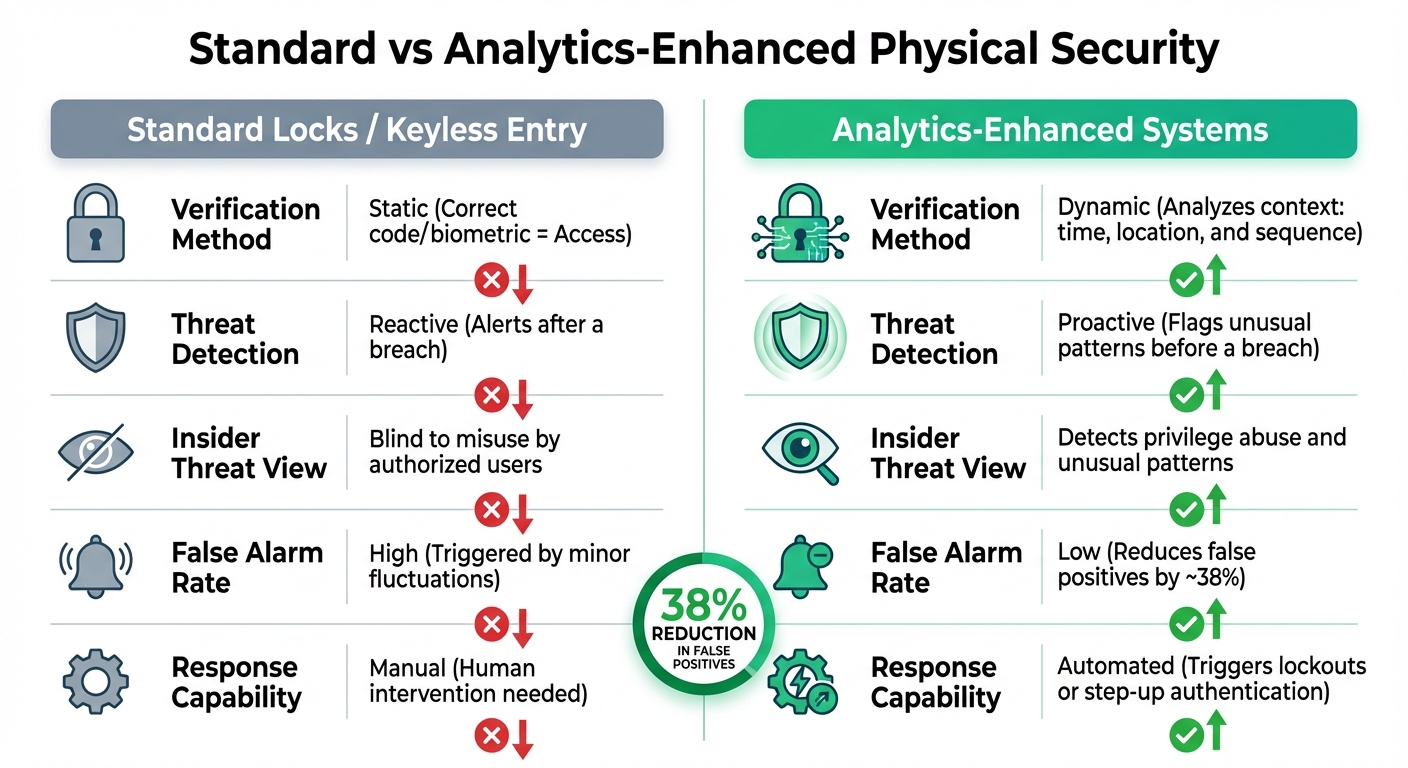
Standard vs Analytics-Enhanced Physical Security Systems Comparison
Behavioral analytics isn’t confined to the digital realm – it’s reshaping how physical security systems function. When paired with technologies like keyless entry, biometric locks, and alarm systems, it shifts the focus from "Who are you?" to "Why does this behavior seem unusual?".
Traditional physical security systems rely heavily on static verification methods. If the correct PIN, badge, or fingerprint is used, access is granted – no further questions asked. Behavioral analytics, however, adds a dynamic layer to this process. It evaluates the context of each access attempt, considering factors like typical entry times, door usage, and carried devices. It even compares these behaviors to those of similar users. For instance, if an employee’s badge is used to access a restricted area at 3:00 AM – far outside their usual 9-to-5 schedule – the system flags this as an anomaly immediately.
Here’s a comparison of standard systems versus those enhanced with behavioral analytics:
| Feature | Standard Locks / Keyless Entry | Analytics-Enhanced Systems |
|---|---|---|
| Verification Method | Static (Correct code/biometric = Access) | Dynamic (Analyzes context: time, location, and sequence) |
| Threat Detection | Reactive (Alerts after a breach) | Proactive (Flags unusual patterns before a breach) |
| Insider Threat View | Blind to misuse by authorized users | Detects privilege abuse and unusual patterns |
| False Alarm Rate | High (Triggered by minor fluctuations) | Low (Reduces false positives by ~38%) |
| Response Capability | Manual (Human intervention needed) | Automated (Triggers lockouts or step-up authentication) |
Take Pittsburgh-based Sherlock’s Locksmith, for example. They install advanced biometric locks and keyless entry systems that integrate seamlessly with behavioral analytics. These systems feed real-time data into centralized monitoring platforms, giving security teams a clearer picture of access patterns. This could reveal, for instance, someone using a legitimate credential to test multiple secure doors in quick succession – often a sign of stolen access. The system can respond automatically, disabling a keycard or requiring additional verification if something seems off. This combination of digital intelligence and physical access control creates a more cohesive and effective security strategy.
One standout feature is treating locks and entry systems as "entities" with their own behavioral baselines, similar to the way digital security systems monitor user behavior. User and Entity Behavior Analytics (UEBA) doesn’t just track individuals; it also monitors physical hardware. For example, it can detect if a smart lock is being tampered with or if access patterns suggest a compromised credential. This dual-layered approach ensures comprehensive monitoring, bridging the gap between physical and digital security.
Conclusion
Behavioral analytics addresses some of the most pressing security challenges today by identifying advanced persistent threats (APTs) and zero-day exploits that slip past traditional signature-based defenses. It does this by spotting subtle deviations from normal behavior patterns, which are often the first signs of trouble. On top of that, it helps reduce alert fatigue by narrowing the focus to high-priority risks.
One of its standout features is detecting insider threats. By flagging unusual activity that deviates from established patterns, it provides a critical layer of protection against internal risks.
Petko Stoyanov, Global CTO at Forcepoint, highlights the value of this approach:
"Given the shortage of skilled cybersecurity talent, behavioral analytics solutions are key capabilities to simplify detection and control access. They also aid less skilled security analysts by highlighting indicators of behaviors of potential suspicious or less trustworthy user accounts or devices."
Beyond detection, behavioral analytics supports regulatory compliance for frameworks like GDPR, HIPAA, and SOC 2. It simplifies these processes by generating detailed, auditable logs and ensuring continuous monitoring.
FAQs
How does behavioral analytics help detect insider threats?
Behavioral analytics takes insider threat detection to the next level by examining usual user and system activity to create a baseline of normal behavior. With the help of advanced machine learning, it flags unusual patterns – such as odd login times, unexpected data transfers, or attempts to access restricted areas – enabling security teams to identify and respond to potential threats swiftly.
This method not only cuts down on false alarms but also ensures that even the smallest signs of insider misuse are caught early, helping organizations safeguard sensitive information and maintain robust security.
How does AI help minimize false alarms in security systems?
AI plays a key role in strengthening security systems by studying normal user behavior and assigning trust scores to identify unusual activity. Over time, it fine-tunes its models to distinguish between everyday behavior and potential threats, helping to cut down on false alarms and avoid unnecessary disruptions.
By weeding out routine or harmless actions, AI ensures security teams can concentrate on real threats, boosting both their efficiency and the overall level of safety.
How does behavioral analytics help with meeting regulatory compliance requirements?
Behavioral analytics plays a key role in helping organizations stay compliant with regulatory requirements by tracking user and device activity to identify unusual or suspicious behavior. This ongoing monitoring strengthens security efforts and creates detailed logs that can be invaluable for audits and reporting purposes.
With a clear and dependable audit trail, organizations can more easily meet compliance standards, showcasing their dedication to maintaining security and accountability.